Discovering the Function of Access Control Solution in Enhancing Security Devices Performance and Efficiency
Access control systems are increasingly recognized as crucial components in the landscape of protection monitoring, offering a structured technique to regulate access to delicate areas and info. Their ability to incorporate with different safety modern technologies, such as monitoring video cameras and alarm systems, substantially enhances the overall performance and performance of security procedures. Nevertheless, as organizations browse the complexities of application and management, various obstacles emerge that warrant consideration. What ramifications do these challenges hold for the future of safety and security protocols and technologies?
Understanding Gain Access To Control Equipment
Access control systems play an important role in making sure the protection of numerous atmospheres, from company workplaces to delicate federal government centers. These systems regulate that can get in or exit a designated location, therefore safeguarding properties and delicate details. The basic parts of accessibility control systems consist of identification, verification, and consent processes.
Identification entails confirming an individual's identification, usually via credentials such as key cards, biometric information, or passwords. As soon as determined, authentication confirms the person's right to accessibility, often through multi-factor verification techniques to enhance protection. Finally, consent determines the level of accessibility granted, permitting for differentiated consents based on functions within the organization.
Accessibility control systems can be categorized right into two main types: sensible and physical. Physical access control pertains to substantial locations, while logical access control regulates electronic information systems. Both kinds work synergistically to supply thorough safety solutions.
Combination With Security Technologies
The integration of gain access to control systems with other safety and security modern technologies is essential for producing an alternative security environment. By integrating accessibility control with video clip surveillance, breach detection, and alarm, organizations can improve their total security posture. This interconnected structure enables real-time monitoring and rapid response to security incidents, enhancing situational understanding and operational performance.
As an example, incorporating gain access to control with video monitoring makes it possible for safety and security employees to validate gain access to occasions aesthetically, ensuring that only accredited people are approved entry. When access control systems are connected to alarm systems, any type of unauthorized accessibility efforts can activate prompt signals, triggering quick action.
Furthermore, the combination of accessibility control with cybersecurity measures is increasingly vital in securing physical assets and delicate information. By lining up physical security methods with IT security systems, companies can make sure that both digital and physical accessibility points are monitored and managed successfully.
Benefits of Improved Safety And Security Operations
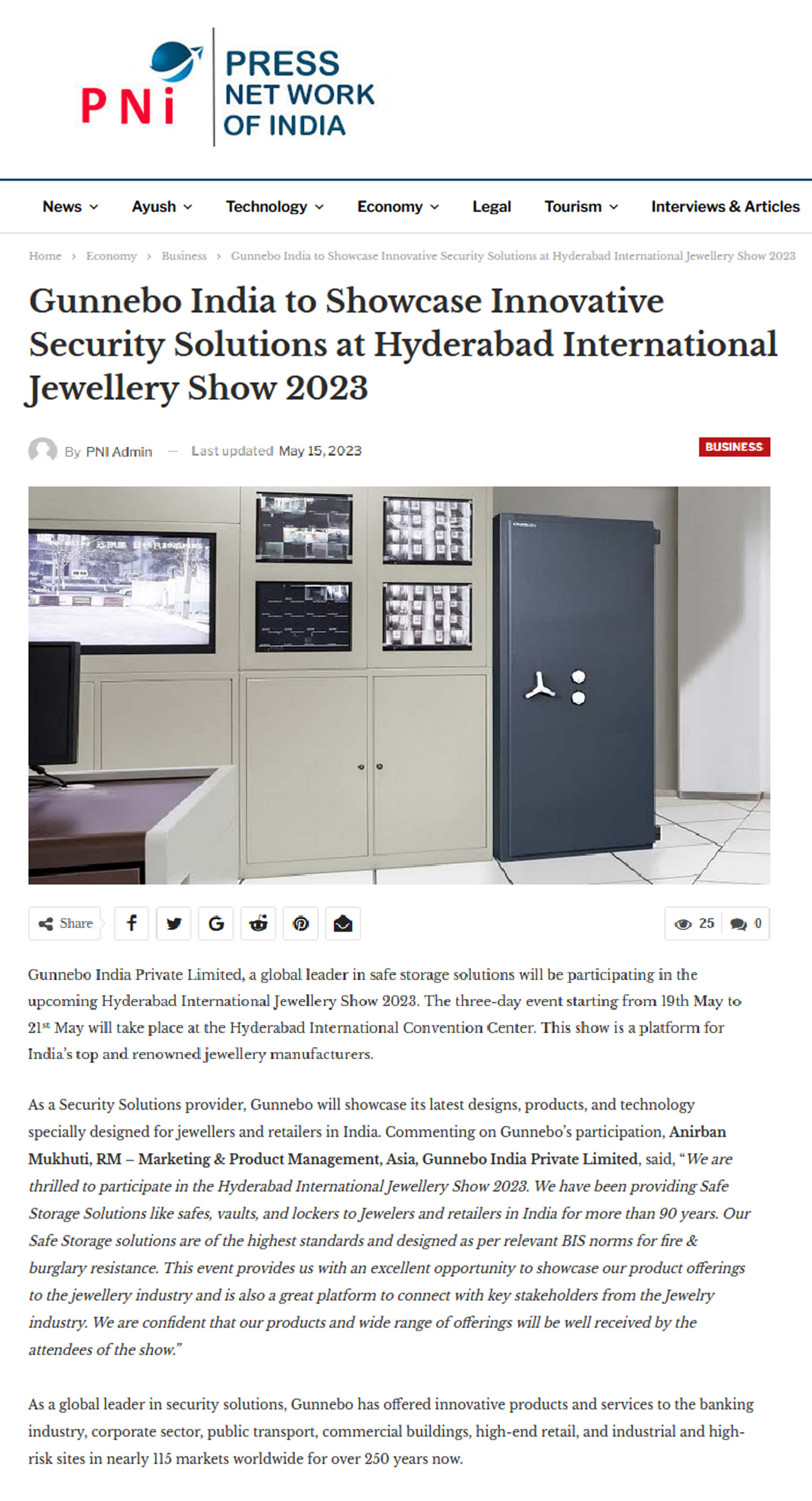
Furthermore, boosted safety procedures assist in real-time monitoring and occurrence feedback. With incorporated systems that encompass surveillance cameras, alarms, and accessibility controls, safety groups can quickly identify and resolve prospective risks. This proactive technique permits timely interventions, reducing the possibility of protection violations and prospective losses.
In addition, reliable safety procedures add to a society of safety within the organization. Workers are most likely to really feel even more safe when they understand that robust look these up procedures remain in location, resulting in increased spirits and performance. The usage of data analytics from gain access to control systems makes it possible for companies to assess protection trends, enhance plans, and designate resources efficiently.
Considerations and obstacles

Furthermore, organizations must attend to the potential for data breaches. Gain access to control systems typically handle delicate info, and read the article any kind look at more info of susceptabilities might subject this data to unauthorized gain access to. access control manufacturers. Making sure durable cybersecurity steps is vital to protect against such risks
User training is an additional vital factor to consider. Workers need to recognize how to make use of access control systems successfully, as improper use can bring about protection spaces. Organizations must balance protection with customer convenience; excessively limiting accessibility can prevent performance and lead to workarounds that compromise security procedures.
Compliance with regulative and lawful requirements is also vital. Organizations must guarantee that their gain access to control systems satisfy industry standards and regional laws, which can vary considerably. Ultimately, the continuous maintenance and monitoring of these systems require committed resources, making it critical for companies to allocate appropriate budget plans and personnel to guarantee long-lasting effectiveness and performance.

Future Patterns in Gain Access To Control
Expecting the future of access control exposes a landscape progressively shaped by technological innovations and evolving safety and security demands. One significant trend is the combination of expert system (AI) and equipment discovering, which boost decision-making capabilities and automate risk discovery. These technologies permit for real-time evaluation of accessibility patterns, allowing even more adaptive and responsive protection steps.
Biometric verification is also gaining traction, with improvements in finger print, facial recognition, and iris scanning modern technologies providing boosted protection and individual benefit. As these systems become much more innovative and budget friendly, their fostering across numerous industries is expected to climb.
An additional arising fad is the change towards cloud-based accessibility control systems. These options provide scalability, remote management, and centralized information storage space, allowing companies to improve operations and enhance efficiency.
In Addition, the Web of Things (IoT) is readied to change accessibility control by making it possible for interconnected tools to communicate and share information, therefore enhancing situational recognition and protection responsiveness.
Final Thought
Finally, gain access to control systems substantially boost the effectiveness and efficiency of protection tools by assisting in exact recognition, authentication, and consent processes (security equipment suppliers). Their integration with surveillance and security system fosters an aggressive protection setting that addresses possible breaches in real-time. While factors to consider and challenges exist, the continuous evolution of accessibility control innovations assures to more enhance security operations. Inevitably, these systems are essential to guarding sensitive areas and information within organizations, making certain a durable safety framework.
Access control systems are significantly identified as necessary elements in the landscape of protection administration, supplying an organized method to regulate accessibility to delicate locations and information. Physical accessibility control pertains to concrete places, while rational gain access to control regulates electronic information systems.The assimilation of accessibility control systems with other safety and security technologies is crucial for producing an all natural security setting. Accessibility control systems often take care of delicate details, and any type of vulnerabilities can expose this data to unauthorized access. Companies have to balance safety with individual convenience; excessively restrictive accessibility can hinder performance and lead to workarounds that endanger safety and security protocols.
Comments on “Innovative Security Equipment from Top Access Control Manufacturers for Your Custom Needs”